Webinar recap: Identifying the latest cybersecurity threats

Implementing practical strategies and tools to secure your company’s data and financials is paramount in today’s threat landscape.
Umpqua Bank is helping businesses protect themselves and their customers from fraud through its series of Success Against Fraud webinars. The third and final installment of the S.A.F.E. series focused on cybersecurity considerations — how to tighten access and create a culture of awareness and vigilance within your organization.
Panel experts included Brian Kindred, Umpqua Bank Chief Information Security Officer, and Ken Nagel, Umpqua Bank Chief Information Officer.
The reasons for a cyberattack can vary, from geopolitical interests and activism to the desire for financial gain. But ultimately, the criminals are after your data and your money so they can extort money or sell the information on the dark web.
The first step toward combating today’s fraud and cybersecurity threats requires focus on four key areas:
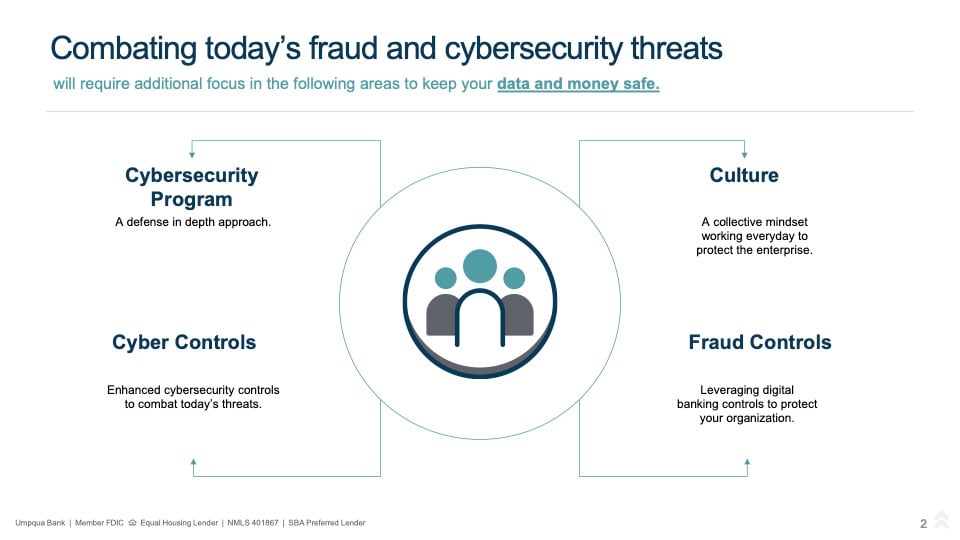
Establishing a top-down culture from the executives is key, says Nagel. “This is an important piece and we’re going to invest in this not only financially but in training.”
In 2023, damages from cyberattacks were estimated to be at least $12.5 billion, a 21% increase from the prior year. And not all events are reported.
Attacks have affected some of the largest companies, including AT&T, Caesar’s Palace, MGM Resorts, Dell, TikTok, Ticketmaster and Kaiser Permanente.
“Half of America’s healthcare data is out there on the dark web,” added Nagel. “And most of our phone number information from the AT&T breach, etc. It becomes really critical that we start putting in some of these programs.”
“Assume breach, and then assume compromise. If you put that as your defense mechanism, you can now put a whole bunch of countermeasures in front of that.”
Block threat actors with education and training
Understanding the types of threats is the first step toward stopping them and protecting your company should it experience a cyber-attack. The threats can begin through phishing or “quishing,” where an email, text or QR code contains a malicious link to trick the victim into visiting what they think is a legitimate site. Once the victim enters their credentials, the criminals can login within one or two minutes, leading to systems being compromised, data stolen or even the installation of ransomware to demand money or risk the slow down or shut down of key systems, devices, services or networks.
The use of QR codes is growing, as the URL is often not fully visible and email systems don’t recognize it. If an employee receives an email with links or a QR code, it’s best to go directly to the website.
Spoofing, lookalike domains and phishing are threats. But your vendors systems could also be taken over and threaded emails compromised and forwarded to a criminal’s address. Phishing training and exercises can help but remind employees to be suspicious if something feels off, or when names and phones numbers are changed, or new payee information is provided. Reconfirm the request directly. Blocking email forwarding can also protect your sensitive email conversations.
To further protect and control access, there is what Kindred called a “trifecta” against credential phishing: usernames and passwords, multi-factor authentications, and devices.
“Tie the device to that system, so that way you can’t login to that system from another device with those credentials.”
Companies can also use their email systems to flag external emails, which helps employees pause and confirm the email’s legitimacy and safety. Work with your technology and cybersecurity professionals to prevent email spoofing and enhance email security systems.
Secure emails and employ identity authentication
Social media is also a source of information for these attacks. In the Caesar’s Palace and MGM cyber-attacks, the criminals used social media to garner information about an employee. They then targeted the company’s help desk, using that information to impersonate the employee and quickly reset the account. From there, they were able to remotely deploy ransomware into the system.
Consider how your help desk authenticates the identity of someone who calls in remotely. Think of new ways to confirm, including multi-passcodes, or a phone call or visual verification through video.
Generative Artificial Intelligence increases the threat
AI has enabled threat actors to quickly replicate an individual with deep fake video or voice or target its victims with automated phishing campaigns. The ability to move fast and scale up quickly can leave companies vulnerable.
Companies will need to protect themselves with awareness and training, and out-of-band verifications, password-less multi-factor authentication, and digital protections like Positive Pay and dual controls, plus a deep defense and incident response including faster patch management.
Third party platforms are at risk
Twenty-three percent of recent attacks have targeted the technology sector, including third-party risk management companies and platforms. It’s critical to understand their inherent risk and level of importance to your organization. Identify security gaps and remediate them. Also, a company needs to understand their contract with these third parties and how they are legally protected. Regular risk assessments and configuration management can ensure strengthened controls.
Companies may also look to add cybersecurity insurance to protect themselves. Ransoms can be expensive compared to the recovery efforts and legal costs that may be incurred.
Ransomware tactics are on the rise
Examples of ransomware trends include double extortion, ransomware as a service, supply chain attacks, unpatched systems and phishing.
Access brokers often steal credentials to sell on the dark web, sometimes to multiple threat actor groups, resulting in more than one extortion occurring.
Ransomware as a service is when a subscription of stolen credentials is sold to other threat actor groups monthly.
Implementing unchangeable backups and testing your backup procedures is one step your company can take to protect its systems from a ransomware attack.
Protect your company’s data and systems
Devising a cybersecurity framework with risk management and layered controls is key. Start with awareness and training. Implement controls. Most importantly, foster an educated and vigilant culture that starts with leadership tone and translates into your corporate strategy.
Access a full replay of this webinar online. To find out more about what fraud prevention tools Umpqua Bank offers, talk to a banker today or visit our website.






